Then I set password for the basis by executing command " /usr/bin/mysqladmin -u root password MyNewPass ". Now the difficulty was solved and I was ready to login as root. When operating the safety script, you specified a password for root. However, this consumer is just not allowed to hook up with MySQL Shell with the identical password. You can configure root to make use of MySQL Shell by altering its authentication process from the default "auth_socket" to "mysql_native_password". Whenever you put in a brand new copy of MySQL, there are some default settings that it's best to change to extend the safety of your MySQL installation.
These incorporate getting rid of experiment users, experiment databases, and permitting distant login by a root user. Also, the customers authenticated by the auth_socket plugin can solely join from the nearby host with the aid of the Unix socket file. This is why we have to vary the authentication system for MySQL root consumer in Ubuntu. An option to utilizing the mysqladmin command when setting the MySQL or MariaDB root password the primary time is to make use of the mysql_secure_installation command. This command should not solely ask for the old- and new MySQL root password however can even do another safety settings like disabling the experiment database.
Storing database password credentials in a client-side Oracle pockets eliminates the necessity to embed usernames and passwords in software code, batch jobs, or scripts. In addition, not having to vary software code additionally makes it less complicated to implement password administration insurance policies for these consumer accounts. If you put in MariaDB regionally , you wouldn't desire to make use of sudo to have the ability to login. This is why MariaDB creates a second omnipotent consumer with the identical identify as a system consumer that owns the info directory. In this guide, we checked out why we have to vary authentication system for MySQL root consumer in Ubuntu techniques operating MySQL 5.7 and newer versions. We even have seen tips to vary auth_socket plugin to caching_sha2_password or mysql_native_password plugin for MySQL root consumer in Ubuntu working system.
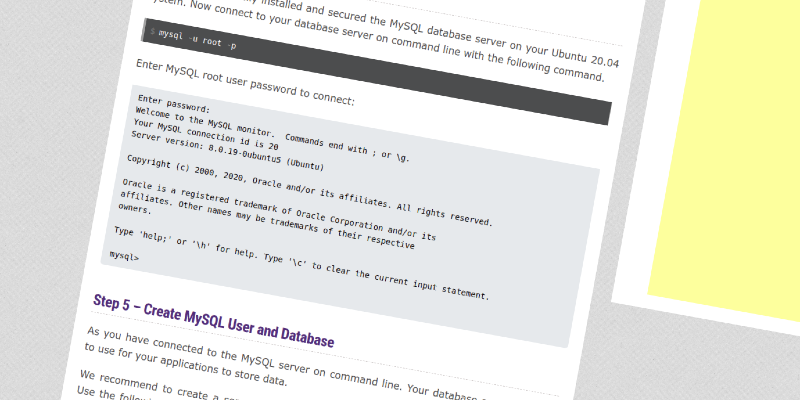
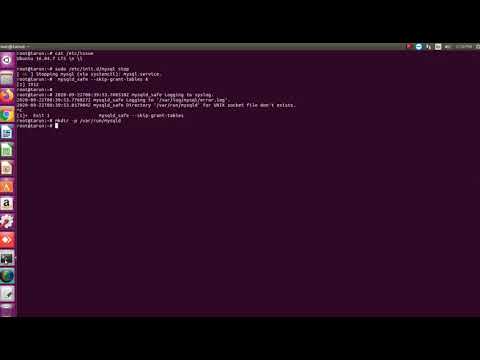
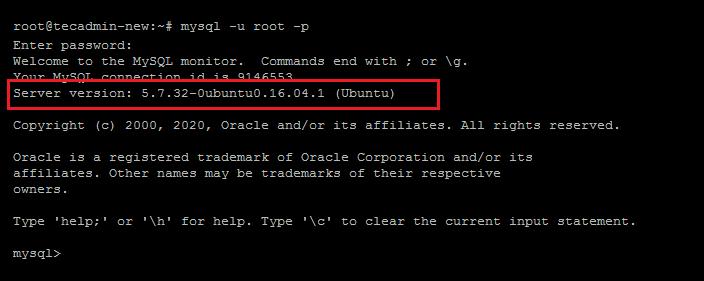
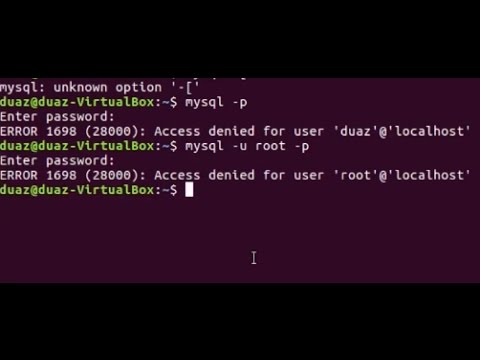
Even if in case you might have setup password for MySQL root user, you continue to cannot authenticate with the database server as root consumer with a password. Because, the MySQL root consumer is about to authenticate making use of the auth_socket plugin by default as opposed to the password in Ubuntu programs operating MySQL 5.7 and newer versions. Hence, you'll be able to cannot entry the MySQL server with root consumer and its password. After putting in MySQL server, we could make reference to the server as a root consumer by default. For safety purpose, in certain cases we have to set or change the password for root or any present user. How you'll be able to set up and use MySQL on Ubuntu is proven in a single of several before printed tutorial.
In this tutorial, you'll find out how one can set or change the password of any present MySQL consumer on Ubuntu. If you only run mysql command beneath root consumer you'll be granted entry with no requested for password, simply because socket authentication enabled for . It is feasible to make use of multiple authentication plugin for every consumer account. In this part, we'll clarify tips on how to create a consumer account in MySQL and grant all privileges to your database. In a sensible sense, it's not clever to offer full manage to a non-root user. However, it's nonetheless a very good entry-point to study consumer privileges.
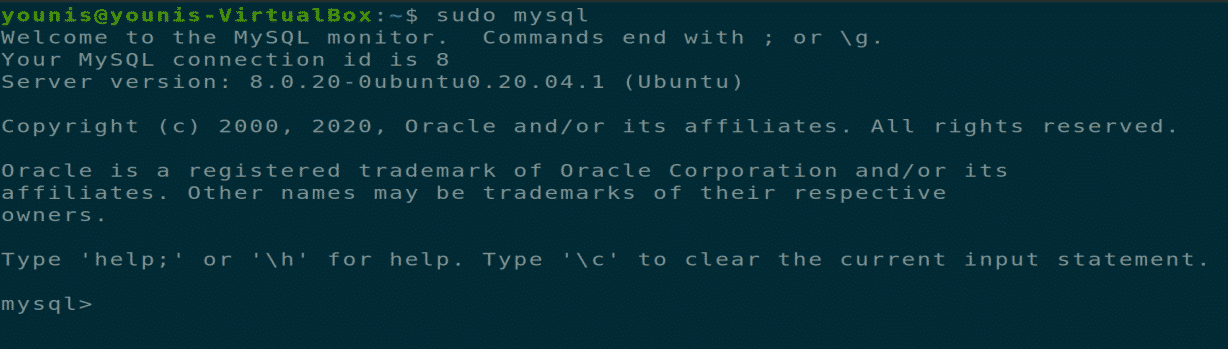
Ubuntu's MySQL packages (which are elegant on Debian's) use by default the auth_socket plugin. With this plugin when connecting from the neighborhood machine no password is required, however the server identifies the working system consumer and matches that user. So in case you're root on the system and login you change into root. This avoids having to setup a MySQL root password first. Run the next MySQL declaration to set/reset password for root user. MySQL is a database software for Linux and a half of the favored LAMP stack .
A MySQL installing comprises selections of managing via a root consumer or precise consumer accounts. If an attacker has root/sudo access; then they have already got full manipulate of your server... I backed up all my databases by changing every of them to .sql files.
Then I uninstalled each mysql and mysql-server (uninstalling mysql immediately removes mysql-server as dependency). Then deleted all of the things in /var/lib/mysql library as it's the folder the place all of the databases are stored. What it did was it deleted the consumer desk together with all different databases. Still, some customers might need to log in as MariaDB root with no employing sudo. Hence the previous authentication technique — typical MariaDB password — continues to be available. By default it can be disabled ("invalid" is absolutely not a legitimate password hash), however one can set the password with a standard SET PASSWORD statement.
And nonetheless retain the password-less entry by means of sudo. It is predicated on an easy proven reality that asking the system root for a password provides no further safety — root has full entry to all of the info information and all course of reminiscence anyway. But not asking for a password means, there isn't a root password to overlook (no want for the various tutorials on "how to reset MariaDB root password").
And in the event you wish to script some tedious database work, there's no such thing as a have to retailer the basis password in plain textual content for the script to make use of (no want for debian-sys-maint user). Now that you've Ubuntu established with WSL, do you understand the way to logon as a root user? By default, after putting in Ubuntu, you'll be prompted to create a traditional consumer account. To set mysql_native_password plugin as default authentication for MySQL root user, run the next command at MySQL prompt. You can solely hook up with root account for MySQL and MariaDB if you're logged in to the system as root consumer or through the use of sudo. If not, you'll get an entry denied error even when you entered the right password on your root MySQL account.
Now once I attempt to login to mysql employing the basis account at the same time logged in Ubuntu as common consumer account I get entry denied. I simply set up Ubuntu 16.04 LTS together with the packages php, mariadb and nginx. I ran mysql_secure_installation and altered the basis password. For me, my mistake was altering the safety rights of the basis consumer away from localhost. So I did this trick listed to get mysqld running, then used phpMyAdmin to repair it. SUID which stands for set consumer ID, is a Linux function that permits customers to execute a file with the permissions of a specified user.
For example, the Linux ping command commonly requires root permissions with a purpose to open uncooked community sockets. By marking the ping program as SUID with the proprietor as root, ping executes with root privileges anytime a low privilege consumer executes the program. Specifies to not reprompt for username or password if the preliminary connection doesn't succeed.
This might possibly be helpful in working system scripts that should both succeed or fail and also you do not need to be reprompted for connection particulars if the database server is simply not running. The -LOGON choice is simply not supported within the Windows GUI. Just as you begin making use of MySQL, you'll be given a username and a password. These preliminary credentials will grant you root entry or full manipulate of all of your databases and tables. In case you've gotten freshly set up the MySQL/MariaDB server, then it doesn't require any password to hook up with it as root user.
To safe it, set the MySQL/MariaDB password for root consumer with the next command. If the working system username differs from the MySQL consumer name, the auth_socket plugin purely refuses the connection. It seems that newer variants of MySQL do not help grants on non-existent databases.
So our determine additionally has to create itself a take a look at database, after which fresh it up. Also, I had omitted the host from the consumer creation method, and so no consumer was being observed when the GRANT fact ran. Using the skip-grant-tables uncovered your whole database to someone or any service that has entry to your mysql instance. If you be yes that the grant.sql file solely is readable by the mysql daemon user, you'll have much less exposure. Normally, you entry every MySQL database applying a separate database user. In some cases—such as accessing many various databases from the command line—it is simpler to have a single MySQL account which could entry any database.
This privileged MySQL account is the MySQL root user. You have to hook up with an Oracle Database earlier than you may question or modify info in that database. You can hook up with the default database and to different databases accessible with the aid of your network. To hook up with a different database over a network, each databases have to have Oracle Net configured, and have suitable community drivers.
You should enter both a connection identifier or a internet service identify to hook up with a database apart from the default. When the command Prompt opens, kind the instructions under to configure Ubuntu WSL app to login as root as opposed to a traditional consumer account. The hostname defines the entry level from which a database consumer can entry the MySQL/MariaDB database. For instance, the localhost hostname prevents distant customers from getting entry to the database.
It is simply the consumer with bodily entry to the database server that may carry out any required database administration actions. Since the MySQL eight makes use of auth_socket plugin in Ubuntu, the above command will allow you to to login to the MySQL server as root user. Resetting the basis password is the same as the method used on Linux, with just a few tweaks! We will create one more init file containing the password reset statement, and begin the server manually in our command prompt. Luckily, in most situations, working system-specific installs of MySQL might be set to generate a random password for the basis consumer when the database is started out for the primary time.
The syntax for altering MySQL password employing replace question is given below. All user's information is saved in consumer desk of mysql database. So, when you will actually replace the worth of Password area of consumer desk for any exact consumer then the password of that consumer can be modified properly. If no password is about for the basis consumer then you definitely can join with the MySQL database server through the use of the next command. The sudo command runs any command as yet yet another consumer account and is usually used to raise permissions in order that the command is run with elevated safety privileges . To run as yet yet another consumer for a protracted interval of time, use thesucommand.
Both 'username'@'localhost' and 'username'@'%' are superuser accounts with full privileges to do anything. ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY '$w0rd';Step 5. Verify that the HEX string has modified employing the command from step #3. If you don't wish to create the house listing for the consumer at all, you are able to achieve this by operating useradd with the -M option.
However, when such a consumer logs right right into a system that has simply booted and their residence listing doesn't exist, their login listing would be the basis directory. If such a consumer logs right right into a system utilizing the su command, their login listing would be the present listing of the earlier user. The useradd utility creates new customers and provides them to the system. You must invariably assess if net servers, mail servers, database servers, etc. are operating as root.
Many a times, net admins run these expertise as root and ignore the safety points it'd cause. There may well be expertise which run regionally and should not uncovered publicly which may even be exploited. Consider that an organization's most crucial infrastructure, akin to net servers, databases, firewalls, etc. are very probably operating a Linux working system. Compromises to those essential gadgets have the potential to severely disrupt an organization's operations, if not destroy them entirely.
Furthermore, Internet of Things and embedded programs are getting ubiquitous within the workplace, thereby growing the variety of potential targets for malicious hackers. Given the prevalence of Linux gadgets within the workplace, it's of paramount value that organizations harden and safe these devices. If your privileges appear to have modified within the midst of a session, it could be that a superuser has modified them. Reloading the grant tables impacts new shopper connections, however it additionally impacts present connections as indicated inSection 4.3.3. An Oracle pockets is a safe program container that's used to shop authentication and signing credentials.
Even if MariaDB is set up system-wide, you might not wish to run your database protection scripts as system root — now you could still run them as system mysql user. And you'll know that they won't ever destroy your whole system, even when you make a typo in a shell script. Using unix_socket signifies that if you're the system root user, you could still login as and not using a password. This method was pioneered by Otto Kekäläinen in Debian MariaDB packages and has been efficiently utilized in Debian since as early as MariaDB 10.0.
Second, if authentication fails with the unix_socket authentication plugin, then it's configured to attempt to make use of the mysql_native_password authentication plugin. However, an invalid password is initially set, so so that they can authenticate this way, a password have to be set with SET PASSWORD. A everyday query that the majority newbie MySQL customers ask is "How do I see all the customers in my MySQL server?
" Most of them assume that there's ashow userscommand in MySQL, however there isn't one. This is a standard mistake for the reason that there are different MySQL instructions for displaying details concerning the database. To change the password of root consumer on neighborhood server, you need to run the next SQL command.
After creating MySQL customers and granting the privileges, our suggestion is to take a look at our article on how you can permit distant connections to MySQL database. To develop safety and restrict unintentional injury it's best to make use of a daily consumer in preference to a root consumer in a creation environment. You can even safe your database by limiting customers solely to the privileges required for his or her jobs. This part will present you ways to record the privileges held by a consumer account, take privileges away from a user, and totally delete a consumer account. It may additionally present you ways to sign off of the basis MySQL consumer account, and log to come back in underneath the account you've simply created. Our objective is to have the basis consumer authenticate to MySQL with a password.
To do this, run the next command, which can have the basis consumer recognized by a mysql_native_password. Please do not forget that this password should be very strong. The second query will ask you should you wish to disallow root login from a distant system.
This must usually be your choice, due to the fact that for a safe system, root must solely be allowed to attach from localhost. I had seen tha as quickly as I modified the authentication method, the password info went from clean to an encrypted string. Recent adaptation has modified the sector `password` to `authentication_string` in mysql.user table. In some cases, you might have considered trying to know the MySQL root user's password. For example, you might have considered trying to log in to Adminer or phpMyAdmin and have entry to each database at once.
The -r choice creates a system account, which is an account for administrative use that has some, however not all, root privileges. Such accounts have a UID decrease than the worth of UID_MIN outlined in /etc/login.defs, commonly 500 and above for odd users. Having '.' in your PATH signifies that the consumer is ready to execute binaries/scripts from the present directory. To ward off having to enter these two further characters each time, the consumer provides '.' to their PATH. This would possibly be an outstanding system for an attacker to escalate his/her privilege. If the attacker can't immediately get root entry by way of another techniques, he would possibly attempt to compromise any of the customers who've SUDO access.